Finding a secure, flexible, and enterprise-level password manager is more than just important, it’s critical to an organization’s security posture. Keeping passwords centralized in a solution designed to integrate with your existing systems through LDAP, such as Active Directory (AD), or single sign-on (SSO) solutions such as SAML providers are a necessity for ease of use and access.
Passwork offers a self-hosted solution with a breadth of features intended to make your organization’s password management easier. Does Passwork work for a modern organization? With my over 20 years of IT experience, I take an in-depth review of the features included in Passwork and in the end give you my opinion of the product.
Passwork has sponsored this product review, but discover their latest features to learn more!
Introducing Passwork Self-Hosted Password Manager
When you think of passwords, you might think of a desktop spreadsheet or text file saved on a trusted employee’s computer. As has been demonstrated over and over, this solution is far from secure for any number of reasons. Ransomware, cracked accounts, and hardware failures are only a few of the potential problems that arise.
Passwork looks to solve that problem by providing a flexible and centralized solution for password management. With role-based access, personal and shared password vaults, along with temporary password sharing combine to solve the problem of the password spreadsheet.
Getting Started by Installing Passwork
Unlike cloud solutions, a self-hosted solution requires an installation on your own systems. The benefit of this approach is complete control over the environment and systems. Data does not leave your network unless requested, and you decide when upgrades and backups occur.
I am evaluating the installation process by installing Passwork onto a Windows Server 2019 Azure VM domain-joined server. Access is restricted to just a standard SSL connection behind a valid certificate.
Diving into the Installation Process
The Passwork application itself is simply a compressed archive (zip) that you extract to a content directory in the Windows Internet Information Services (IIS) webserver. In addition, you’ll need a license file which you may obtain via a free trial.
Although the installation of Passwork is simple, it’s the supporting pieces that take the bulk of the installation time. As Passwork does not currently have an integrated installer to handle this on Windows, you are required to individually configure each component which may be prone to error.
Passwork is actively working on an integrated installer to make the process much simpler!
In this case, you must install PHP, the IIS Rewrite module, MongoDB (for the backing database), and several supporting utilities. The challenge is bringing together the most secure combination of components. PHP is recommended to be installed via the Web Platform Installer, but this will be no longer supported at the end of 2022. PHP 7.3 is the current recommended version, but this particular version is also end-of-life.
Though PHP 7.3 is used in the current version, PHP 8.0 support is coming along with updated components. With this change, and previously noted integrated installer, the process to get started will be much quicker and more secure.
Securing the Passwork Installation
Passwork offers instructions on securing the MongoDB installation along with putting Passwork behind an SSL certificate. But, securing MongoDB (assigning an administrative password) is a separate document and not mentioned in the main installation guide as recommended, which I do think is important if not necessary for any MongoDB installation.
As shown below, securing MongoDB is a manual process that should ideally be included in a comprehensive installer. Passwork has written a guide on securing the connection, so the documentation is available to those doing the install.
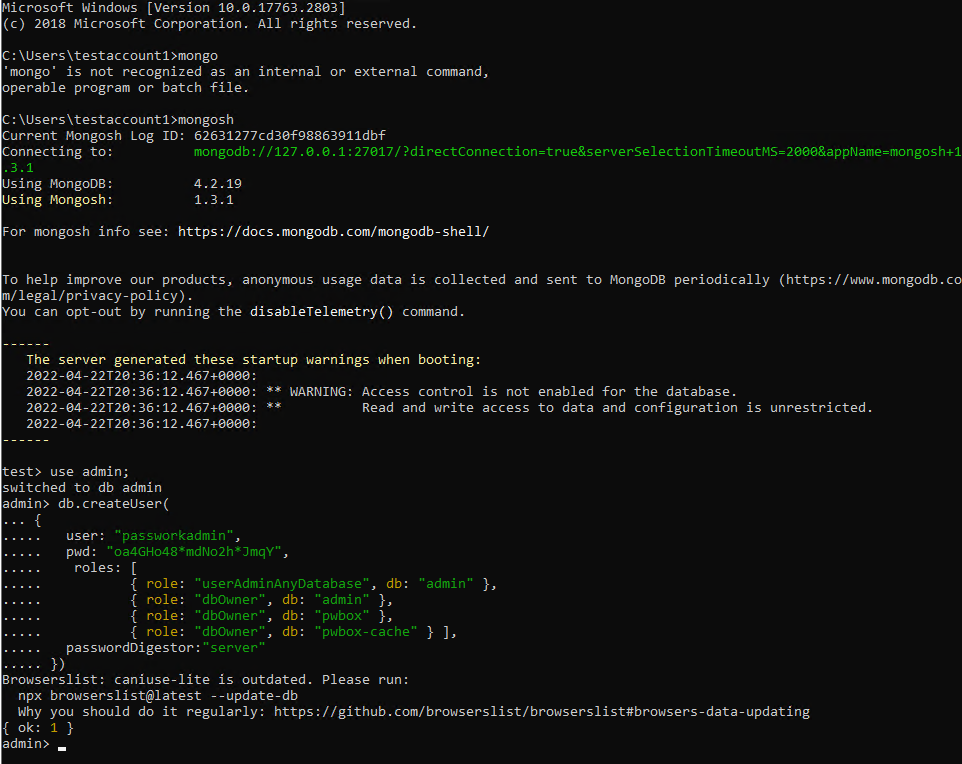
In addition, SSL is considered optional, but I personally would like to see that made mandatory. This does make the product slightly less flexible, but in today’s environment security should be paramount.
First Start of Passwork
After all required components are configured and installed, you simply need to navigate to your installation URL to get started. You are presented with the database connection prompt first and ultimately presented with a sign-up screen. The process is quick, but it’s important to note that the first user entered becomes the organization owner.
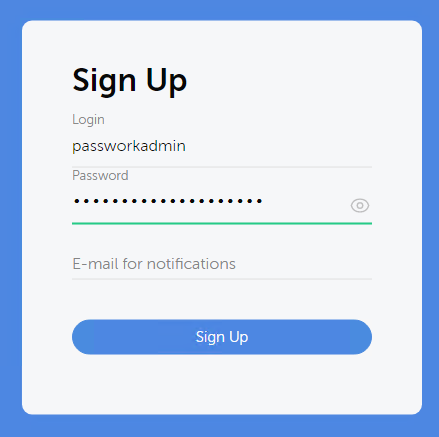
The two concerns I had here are that there is not a password confirmation prompt and that there is no help text noting the importance of this user. Neither is critical, but it would help to inform the installer that they should not take this user lightly. The owner registration process is quick and allows you to jump right into using Passwork.
Creating Your First Vault and Password
With Passwork installed, it’s time to create a vault and store some passwords! Once logged in, you are presented with the opening screen requesting to create your first vault. You will notice that there are two types of vaults on the left-hand navigation menu. Organization Vaults are shared between team members, while Private Vaults are intended for personal usage.
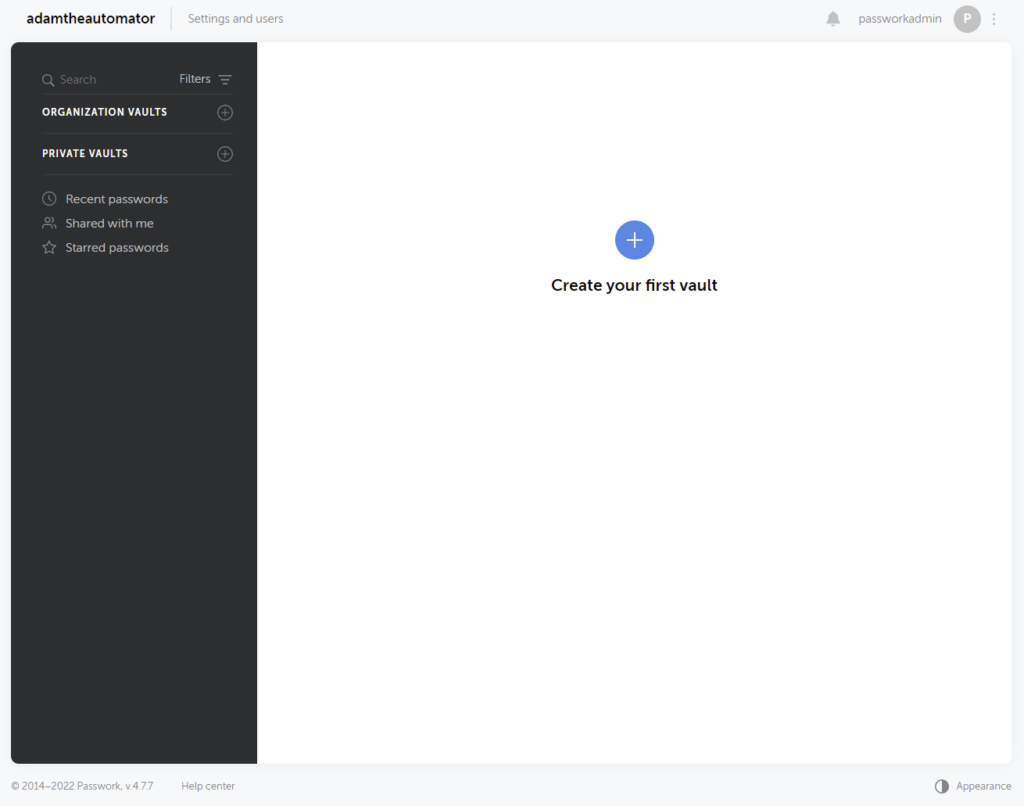
What is a very handy feature is that you can promote a Private vault to an Organizational vault at any time. This is not a feature I’ve typically seen on other password managers. In addition, for a Private vault, you are also able to invite other users and create password-sharing links, the same as you can with an Organizational vault.
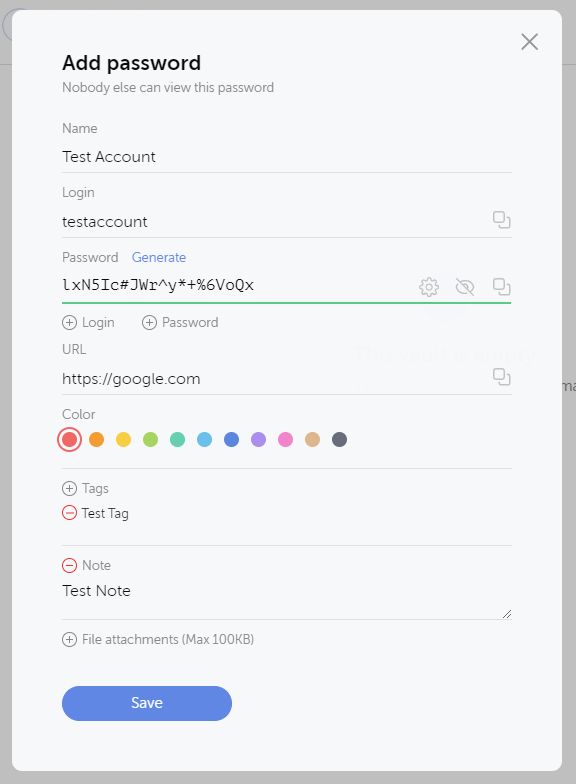
In my testing, I created a simple Password organizational vault, and I’ve created a new entry for a password. I used the built-in generator for the password, which has the typical features to exclude special characters and similar characters. In addition, you are able to color-code, tag, and add notes to your password entry.
For each password entry, you can also add a large number of additional logins and passwords as well. If there are alternate entries, this adds flexibility. At first, I had difficulty finding a way to add arbitrary data, to store license data, for example. If you click the plus sign next to the Login or Password fields, you can add a new data field and rename the title to reflect the stored data.
Bring Everyone Together With Shared Passwords
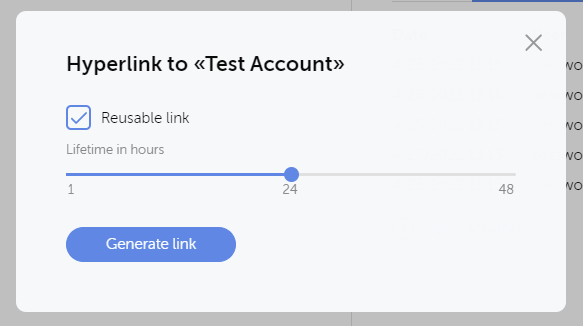
Often times you may have a contractor that temporarily needs access to a password. With Passwork, you can create a temporary link (potentially reusable) with a specified access lifetime. What isn’t clear is what a “Reusable link” actually means. If it’s reusable does that mean that there is a cookie-based timeout for an IP or that it is one-time access only? I was unable to determine that, so the documentation could be improved here.
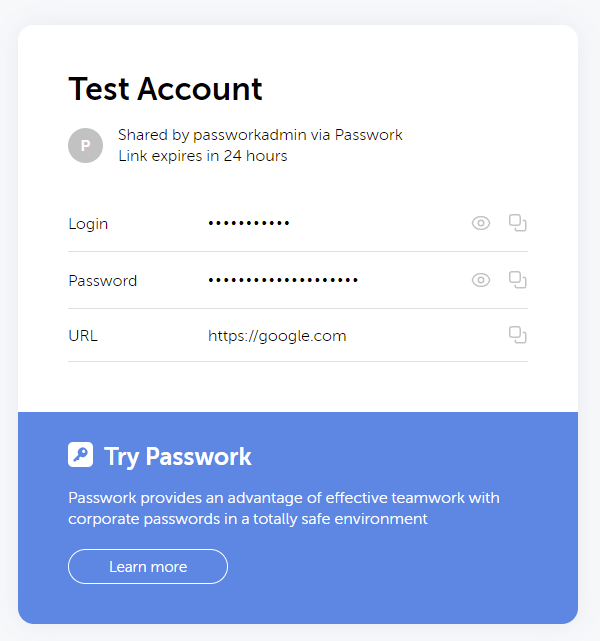
Once shared, an end-user does not actually need to authenticate to an account, they simply need the link. I see benefits in this approach as you are able to share necessary passwords without creating a one-time account and thus using a license. But, since there is no required authentication, the audit logs only show that the account was accessed but not by which specific user (shows a blank entry), which does pose difficulties in auditing.
Managing Users and Roles
Any modern enterprise product needs the ability to manage both users and roles. Passwork offers both users and assignable roles. There are a number of assignable permissions, for both vaults and folders contained within. This flexibility allows an administrator to specify just what passwords are available to a given user or role.
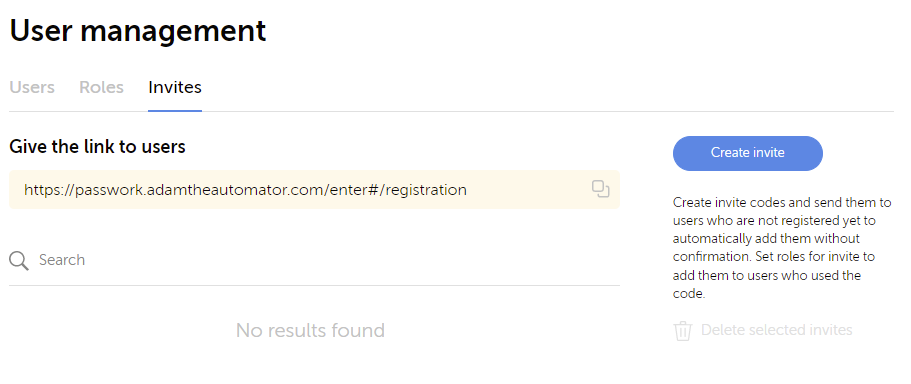
First, a user will have to sign-up. When this happens they will have an invitation that must be approved. This is applicable only if you have the setting of “Any user can sign up…” checked or any of the “Automatically confirm new users…” settings for local accounts, LDAP, or SSO unselected.
Once users are added, they only have three levels of permissions as outlined below:
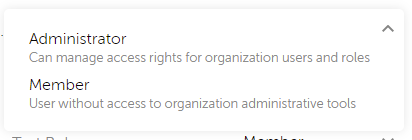
- Member – User without access to organization administrative tools.
- Administrator – Can manage access rights for organization users and roles.
- Owner – Special permission that only a single user can have and has access to all aspects of Passwork.
The Owner permission can be re-assigned to another user, but what would typically be advised is that this permission is assigned to a service local account. If this would be SSO or LDAP and that authentication system is unavailable, you may not be able to log into Passwork as an Owner.
For assignable permissions, available for both users and roles, the below offer flexibility and correspond to most common permission schemes.
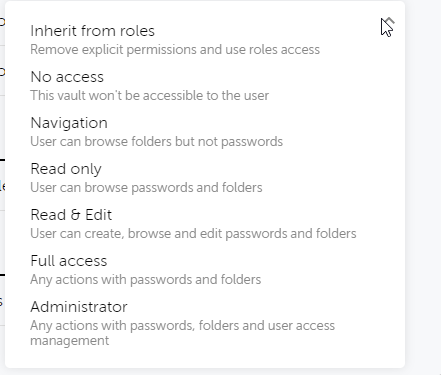
- Inherit from roles – Remove explicit permissions and use roles access.
- No Access – This vault won’t be accessible to the user.
- Navigation – Users can browse folders but not passwords.
- Read Only – Users can browse passwords and folders.
- Read & Edit – Users can create, browse, and edit passwords and folders.
- Full Access – Any actions with passwords and folders.
- Administrator – Any actions with passwords, folders, and user access management.
One quirk is that you are unable to just delete the access level entirely from a resource, therefore you must explicitly assign “No Access”. I personally would prefer the ability to delete the entry as this clutters over time, but the one benefit may be that you maintain the history at a glance.
You are unable to share an individual password to a role, you can only assign an individual password to a user.
Securing Vaults, Folders, and Passwords
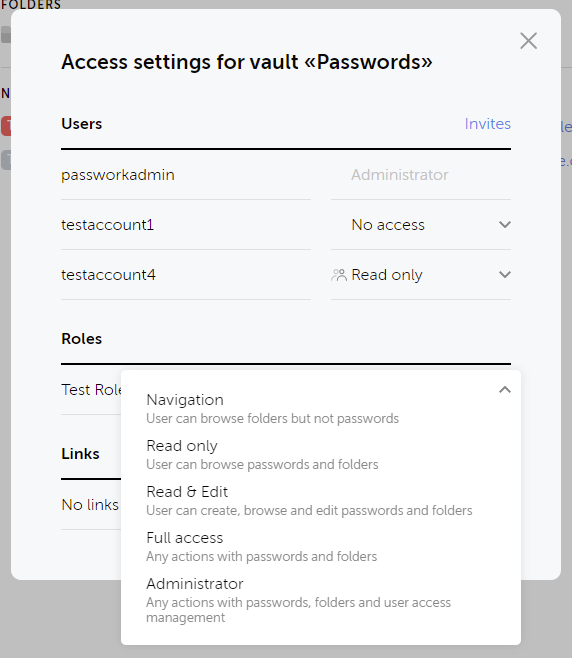
With users and roles defined, I needed to limit access to either a vault, vault folders, or individual passwords themselves. Passwork makes this pretty easy, as you can define these permissions in one of two places. As you can see below, my passworkadmin owner account inherits Administrator access, but the testaccount1 is explicitly denied access, and testaccount4 has only read-only access.
To avoid individually assigning permissions to each and every account, I can add a role, in this case, the Test Role with the specified access.
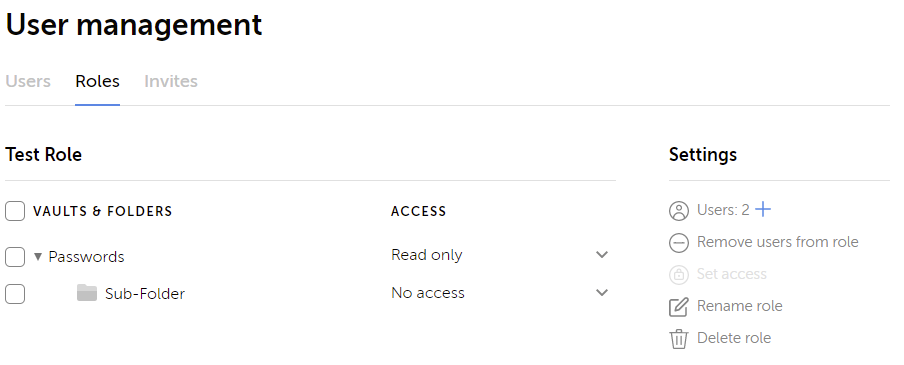
The other location to manage access for a role is under the Settings → User Management → Roles section. As shown below, I have given the Test Role Read only access to the Passwords vault but denied access to the folder named “Sub-Folder”.
This flexibility is handy, but one thing to note is that the access changes are instant. There is no way to configure and then save the role changes. Therefore you need to be careful when making changes as they may impact users as your work.
Web Extension and Mobile Application
As is standard with modern password managers both a web extension and mobile application are available for password management on the go and during daily operations via your browser. Save time by avoiding logging into the main web application and retrieve your password resources in the most convenient method for you.
Stay Productive with the Web Extension
Though you can do most operations necessary in the web application, you are unable to save attachments from the extension itself. This does necessitate using the web application. The web extension offers plenty of functionality for day-to-day operations without needing to open the web application itself.
The web extension will auto-complete logins for websites and allow quick access to your passwords. along with providing a password generator for new ones. As shown below, I am retrieving a simple password by clicking on the extension, navigating to a vault, and choosing the entry I need.
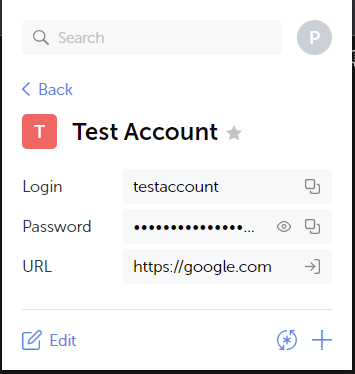
Navigating Passwords on the Go with the Passwork Mobile Applications
The mobile application is responsive, full-featured, and available on both Android and Apple products. As is the case with the web extension, you can do most options within the mobile application. But, similar to the web extension, you are unable to add an attachment or multiple login/password values for an entry.
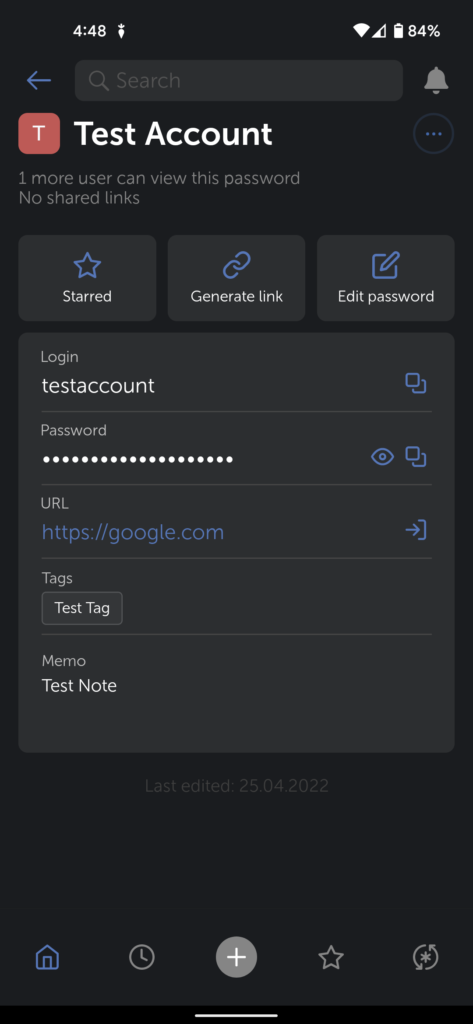
To secure the mobile application, biometric and PIN code authentication is enabled. If your device supports biometrics, that is by far the most secure way to go and worked flawlessly in my testing. By starring password entries, quickly access the most important passwords as you need.
Going Further: LDAP (Active Directory) and Single Sign-On (SSO)
No enterprise application would be complete without integrations into an organization’s authentication system and Passwork is no different. Offering both LDAP (typically Active Directory) and SSO (Single Sign-On) options, there is flexibility in how an account can access their Passwork resources.
Integrating LDAP for Active Directory Support
I tested the integration with Active Directory via the LDAP integration. First, you will need to set up your server. You can authenticate against more than one LDAP server differentiated by the server code (i.e. the suffix of the user such as testaccount1@otherldap). In my case, I had one AD environment to authenticate against which was configured as below.
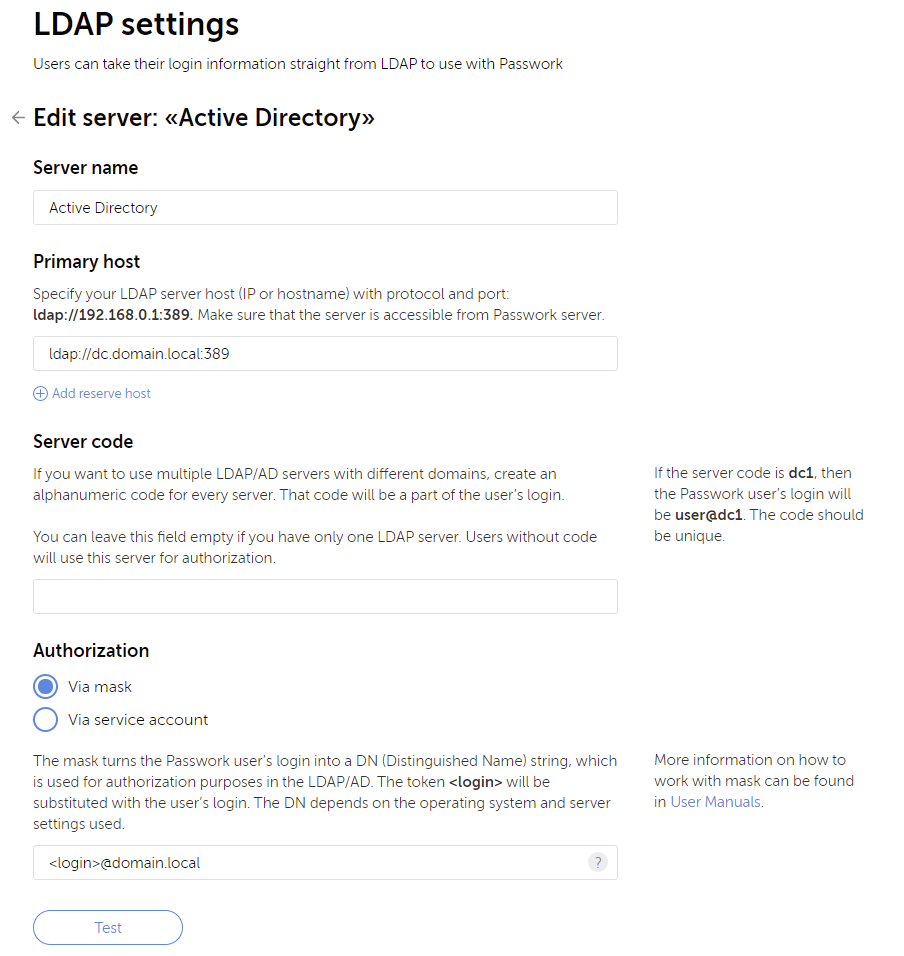
A useful feature is the ability to automatically confirm LDAP (or SSO) users. This means a user who has not ever signed in will not need to confirm their account. In addition, you are then able to define a DN (Distinguished Name) of the OU (Organizational Unit) to import groups of users. This means that I was able to automatically assign all users in the Passwork Users group to the Test Role.
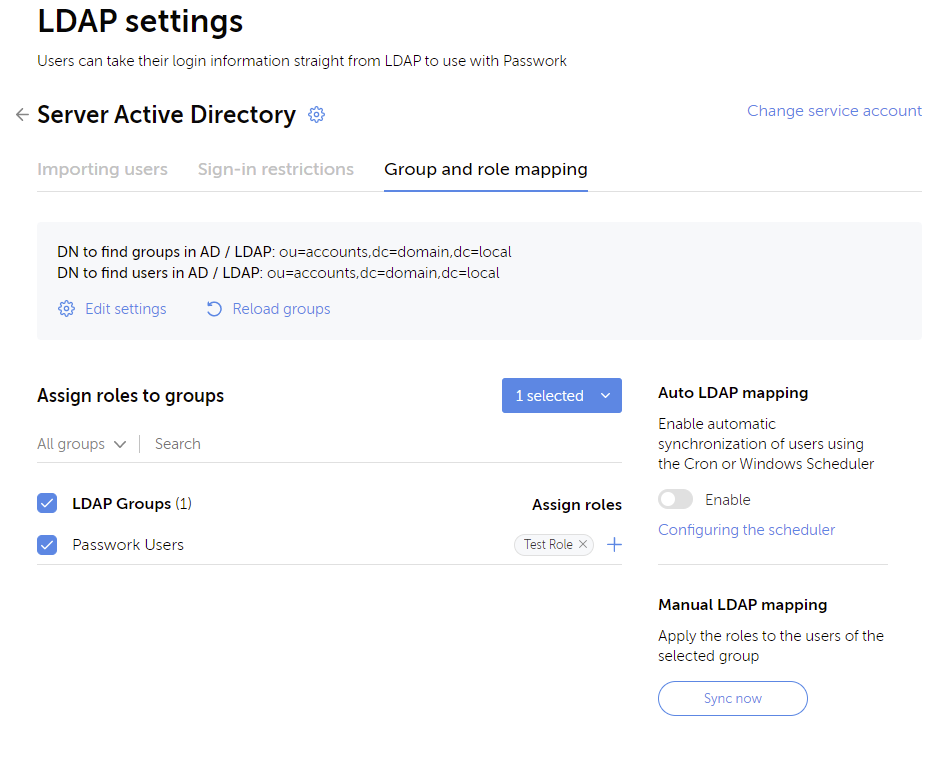
You are able to run a manual sync or set up an automatic mapping on a schedule via Windows Scheduler or a cron job for Unix-based systems. But, what I would ideally like to see here is that upon login, the user’s group membership is then queried to assign the role at the time of sign-in. Without this, you potentially have the ability to sign in as a new user but not have access to any resources until the sync is run.
Simplify Logins with Single Sign-On (SSO)
Similar to how LDAP works, integrating Passwork with SAML allows one-click logins (provided you have already authenticated) or the use of your own authentication system. To configure SSO I used the Azure AD SAML Toolkit to utilize Azure Active Directory as the authentication provider.
The main challenge here was determining what value to use for the certificate. You cannot upload a certificate that your SSO system may give you, nor does it indicate what encoding is necessary. In this case, you need to use a Base64 encoded value. This is provided by the Azure AD SAML Toolkit, but with a heading value of ----BEGIN CERTIFICATE-----. If you do not strip that header and trailer off, then the validation will fail. This would ideally be made clear in the documentation and the interface.
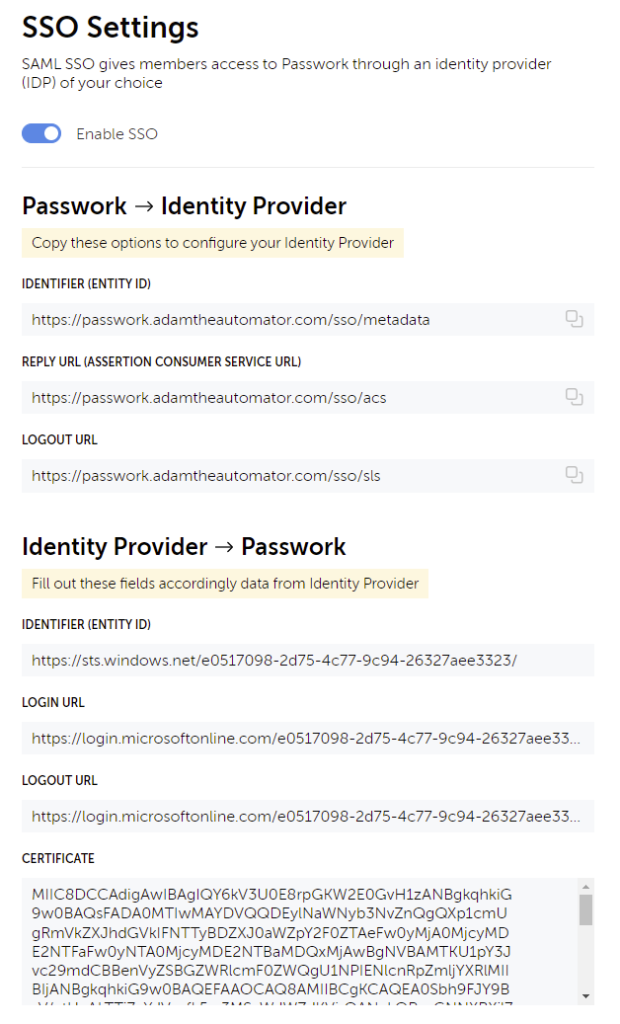
Once configured, you will see that a new button is added to the login screen “SSO Login”. Once clicked you will either be automatically redirected to an authenticated Passwork session or taken to your external SAML authentication provider. As I was already logged into the Azure AD Portal, I immediately authenticated and was directed to the main Passwork screen.
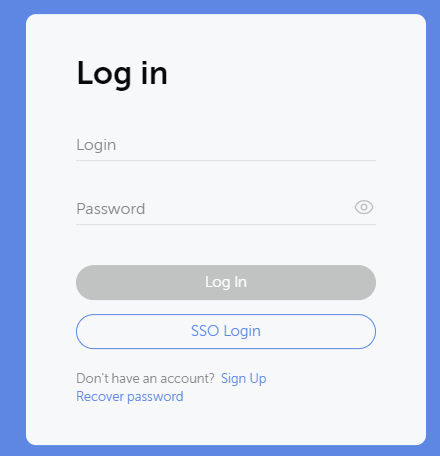
The only feature that I personally would want to see here is authorization mapping to groups, much like LDAP integration has. Without this, you will need to assign a newly authenticated user to a group manually once they have logged in for the first time.
Extending Passwork via the API
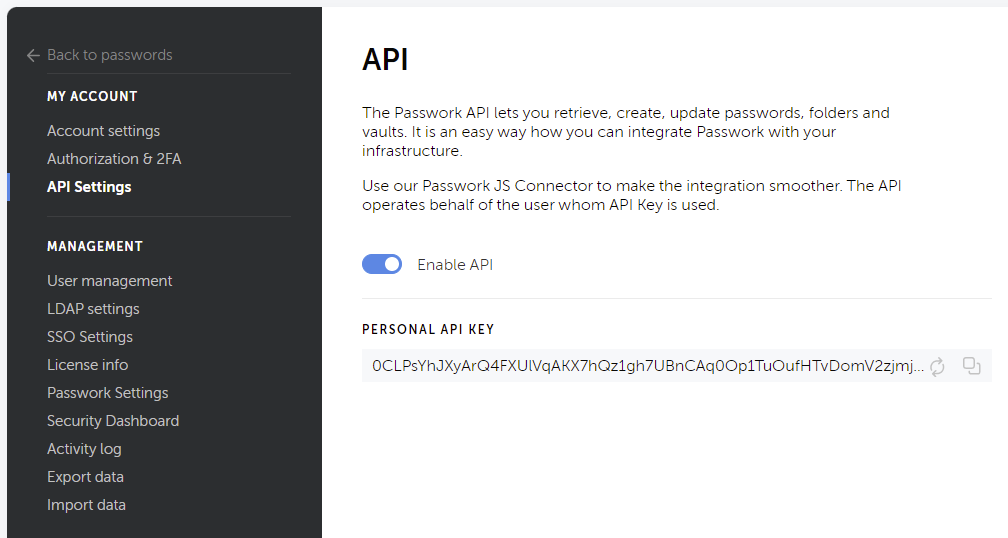
To make password management even more extensible, Passwork includes a comprehensive API that covers most operations available through the interface. First, you will need to create a Personal API Key available from the My Account settings.
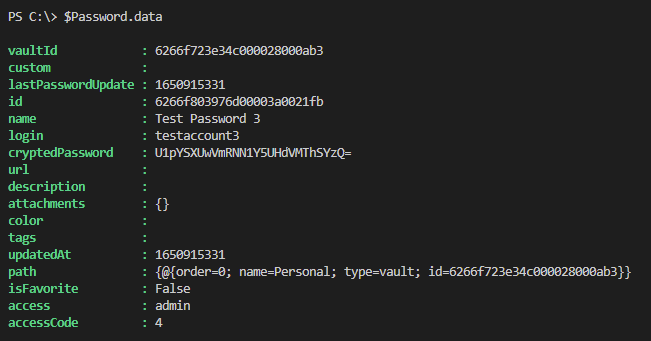
To illustrate how the API works, I wrote a short PowerShell script that retrieves an authentication token, list available vaults, retrieves the password in a given vault, and ultimately the password entity itself.
$APIKey = '0CLPsYhJXyArQ4FXUlVqAKX7hQz1gh7UBnCAq0Op1TuOufHTvDomV2zjmjBr'
$APIURI = 'https://passwork.adamtheautomator.com/api/v4'
$Params = @{
"URI" = ("{0}/auth/login/{1}" -F $APIURI, $APIKey)
"Method" = 'POST'
}
$Token = Invoke-RESTMethod @Params
$Params = @{
"URI" = ("{0}/vaults/list" -F $APIURI)
"Method" = 'GET'
"Header" = @{
'Passwork-Auth' = $Token.Data.Token
}
}
$Vaults = Invoke-RESTMethod @Params
$Params = @{
"URI" = ("{0}/vaults/{1}/passwords" -F $APIURI, $vaults.data[0].id)
"Method" = 'GET'
"Header" = @{
'Passwork-Auth' = $Token.Data.Token
}
}
$VaultPasswords = Invoke-RESTMethod @Params
$Params = @{
"URI" = ("{0}/passwords/{1}" -F $APIURI, $VaultPasswords.data[0].id)
"Method" = 'GET'
"Header" = @{
'Passwork-Auth' = $Token.Data.Token
}
}
$Password = Invoke-RESTMethod @Params
$Password.data
Conclusion
Passwork offers many common features that one expects in an enterprise Password management solution. This self-hosted option alleviates many of the concerns that follow increasingly common cloud-hosted platforms, such as data privacy and control. With a full-featured API, password management options, and advanced integration to LDAP and SSO, Passwork offers a compelling alternative to many existing Password management solutions out there.
I would recommend Passwork for those looking for more control in a self-hosted platform. Though there are not an over-abundance of features, what are available work well and cover most bases that are needed in a modern enterprise password management solution!




