Finding security vulnerabilities in systems and patching them has become one of the most important jobs for network administrators. Metasploit is a popular exploitation tool that helps security professionals find and expose system vulnerabilities.
In this tutorial, you will learn how to install Metasploit on Ubuntu and use it to scan for vulnerabilities in your systems.
Read on to never worry about a system’s security again!
Prerequisites
This tutorial will be a hands-on demonstration. If you’d like to follow along, be sure you have
- An Ubuntu Linux system. This tutorial uses Ubuntu 20.04, but any recent version should work fine.
- You will also need root privileges on your system to install Metasploit. This tutorial uses a root account, but for security purposes, it is recommended that you use a sudo-enabled user.
Installing Metasploit Using the Shell Script Installer
The official Metasploit shell script installer is the quickest way to install Metasploit on Ubuntu. This method works on any Debian-based system, including Ubuntu. This shell script takes care of all the dependencies and configuration for you.
1. Run the following wget command to download the latest version of the Metasploit installer from GitHub.
wget http://downloads.metasploit.com/data/releases/metasploit-latest-linux-x64-installer.run
2. Verify that the file download was successful by listing its contents.
ls -la metasploit-latest-linux-x64-installer.runYou will see a similar output below.
3. Before you can run the installer, you need to make the file executable. Run the following chmod command to give the installer file executable permissions.
chmod +x ./metasploit-latest-linux-x64-installer.run4. Now, you can run the installer by pretending the name with ./.
./metasploit-latest-linux-x64-installer.run5. Press Enter to read the Metasploit license agreement
6. Type y and press Enter to accept the terms and continue.
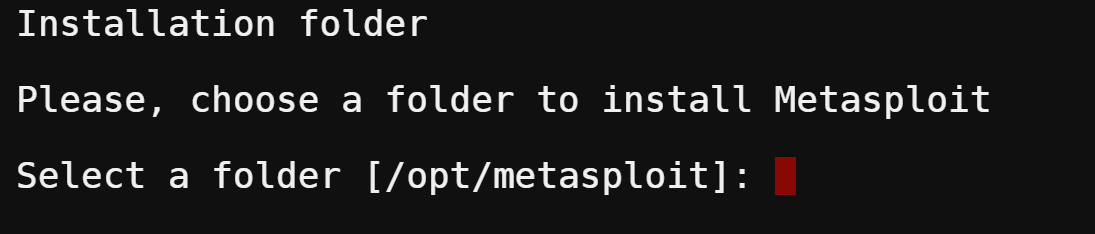
7. Select a folder to install Metasploit. For this tutorial, you will leave the default installation directory at /opt/metasploit and press Enter to continue.
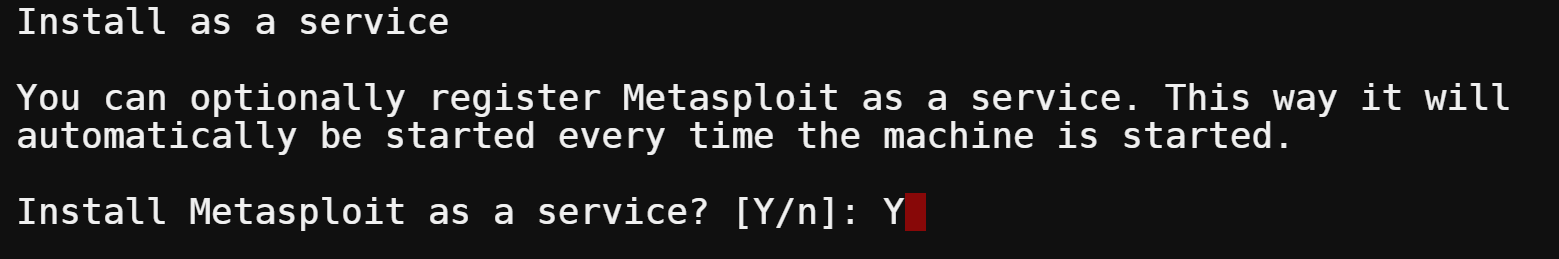
8. To install Metasploit as a service, type Y and press Enter.
By default, Metasploit will not run as a service. You can start, stop, and restart Metasploit from the command line manually, or you can install Metasploit as a service. Installing Metasploit as a service will allow it to start automatically when your system boots up.
9. Metasploit uses some techniques that could be flagged by your antivirus or firewall program. To avoid any issues, it is recommended that you disable these programs while working with Metasploit. To Disable Anti-Virus and Firewall, press Enter.
10. Enter the port that you want Metasploit to use. The default port is 3790, but you can choose any open port on your system. For this tutorial, you will be using the default port of 3790. Press Enter to continue.
Choose a port over 1000 and non-standard to avoid potential conflicts with other programs.

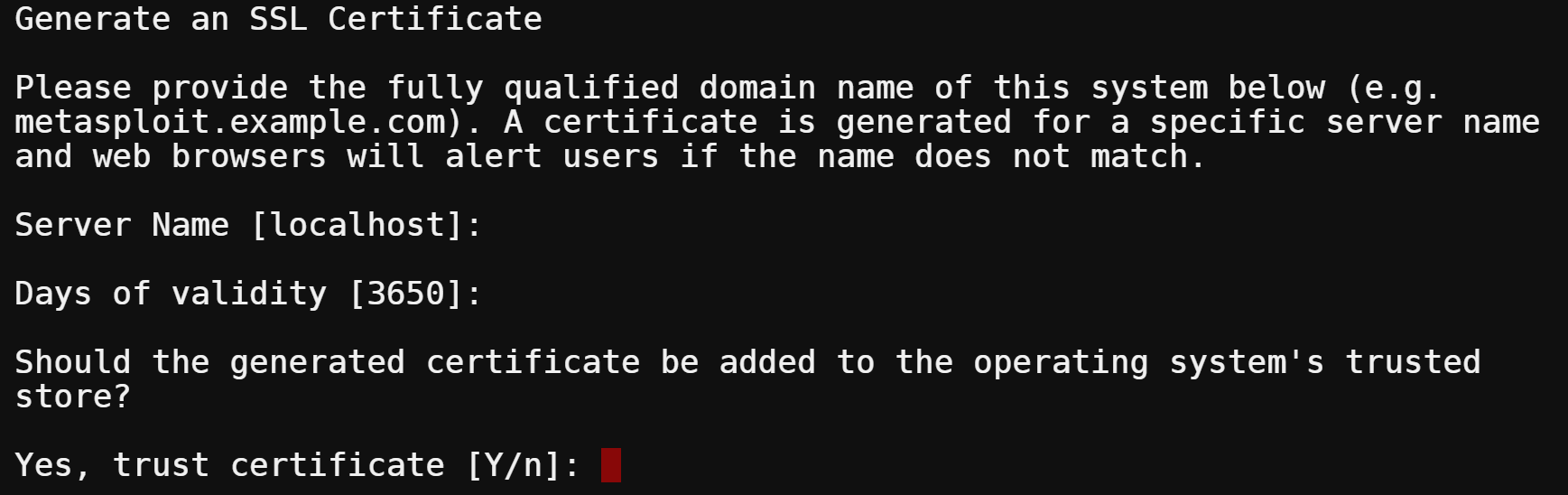
11. By default, Metasploit will use localhost as the Server Name. For this tutorial, leave the default and press Enter to continue.
12. The Metasploit shell script installer will default generate and install an SSL Certificate valid for 3650 days (10 years). For this tutorial, you leave the default value of 3650 days and press Enter to continue.
13. The script will generate a self-signed SSL Certificate for Metasploit. Type y to trust the certificate and press Enter to continue.
14. Finally, type Y and press Enter to start the Metasploit installation process.
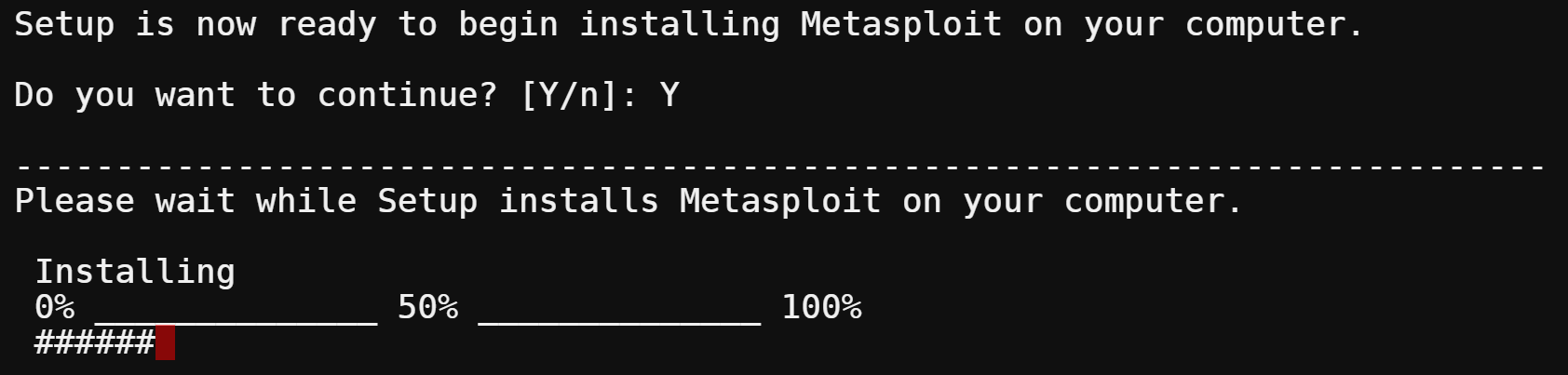
15. Wait for the installation to complete. Once the installation has finished, you will see a message that says go to https://localhost:3790 from your web browser to access the web UI. You have successfully installed Metasploit on your Ubuntu system.
16. Open a web browser and navigate to https://localhost:3790 to load the Metasploit web interface.
17. To access the Metasploit console from the command line, run the below command.
msfconsole
Installing Metasploit From Source
Why would you want to compile and install Metasploit from the source? Maybe you want the latest features that have not yet been released in the shell script. Or maybe you are developing a new module for Metasploit and need to test it.
But, this method requires manually downloading and compiling the source code, which can be a bit tedious. Follow the steps below to compile and install Metasploit from the source on your Ubuntu system.
1. Run the apt command below to update your package list to ensure you have the latest versions.
apt update -y
2. Install all of the required dependencies for building and installing Metasploit.
apt install gpgv2 autoconf bison build-essential postgresql libaprutil1 libgmp3-dev libpcap-dev openssl libpq-dev libreadline6-dev libsqlite3-dev libssl-dev locate libsvn1 libtool libxml2 libxml2-dev libxslt-dev wget libyaml-dev ncurses-dev postgresql-contrib xsel zlib1g zlib1g-dev -y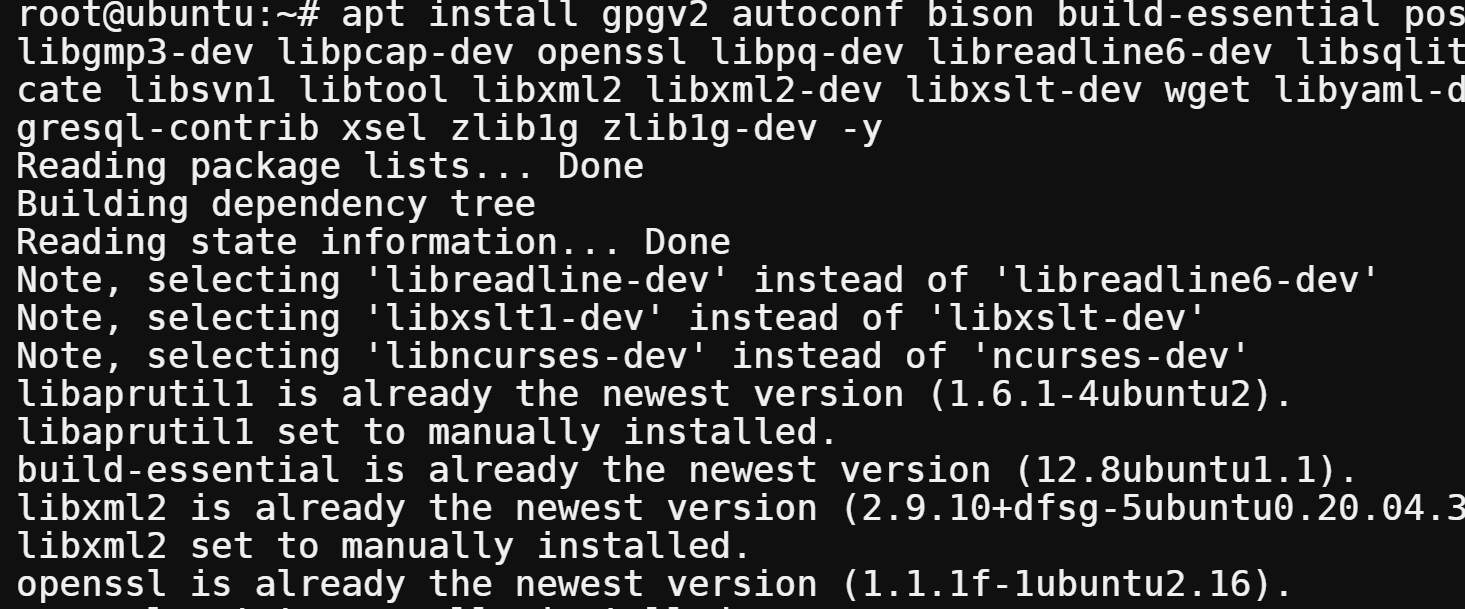
3. Next, download the Metasploit source code by running the following command. This command saves the Metasploit source code to a file named msfinstall in your current working directory.
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall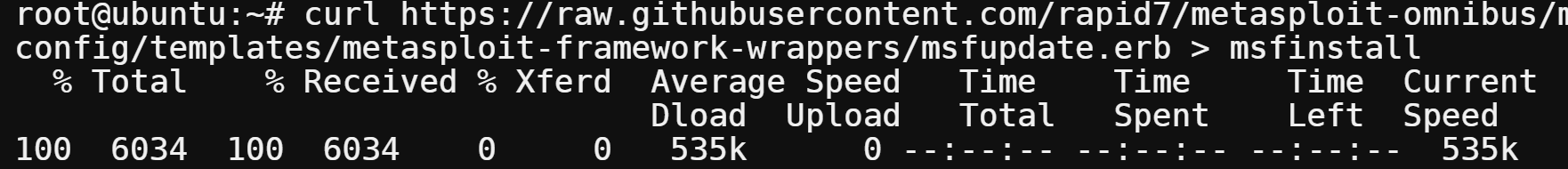
4. List the file to confirm you’ve downloaded the file successfully.
ls -la msfinstall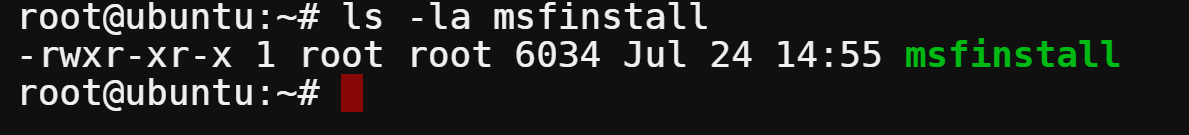
5. Before you can run and compile the source code, you must ensure that msfinstall is executable.
chmod 755 msfinstall6. Finally, run the code to start the Metasploit installation.
./msfinstallThe installation process could last several minutes, depending on your system resources.
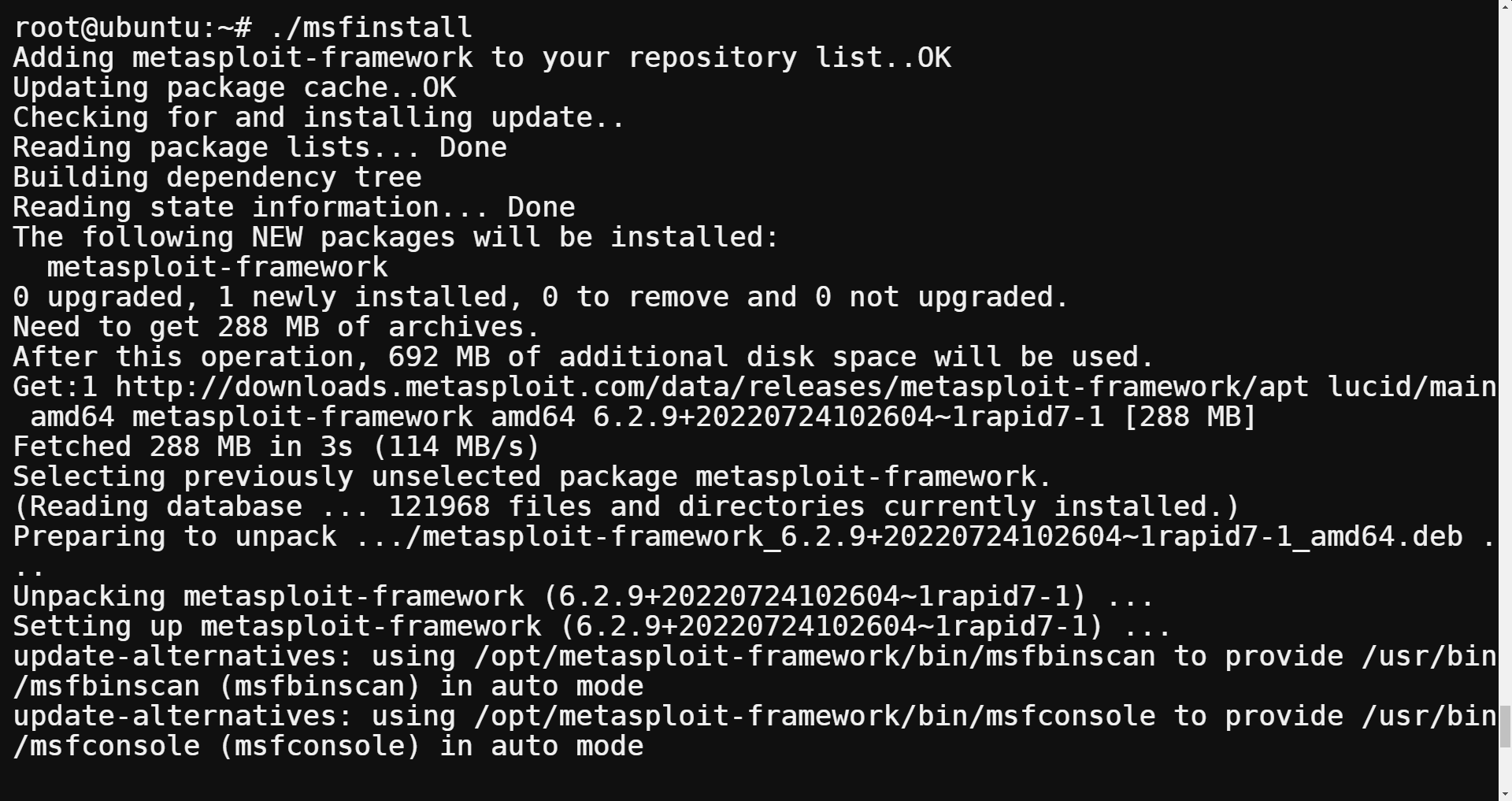
7. Access the Metasploit console and start using it.
msfconsole
Installing Metasploit on Ubuntu Using Deb Package
The reason to use a deb package is that you can install it offline. You do not need an active Internet connection to install Metasploit.
A deb package is an archive file containing all the files required to install a software application on Debian-based systems. A deb package is a software installation file, similar to an executable (exe) file on Windows.
Related: Comprehensive Guide to Installing Deb Packages on Ubuntu
Follow the steps below to install Metasploit on your Ubuntu system using a deb package.
1. Download the Metasploit deb file from the Metasploit download page.
wget https://apt.metasploit.com/pool/main/m/metasploit-framework/metasploit-framework_6.2.8%2B20220720103055~1rapid7-1_amd64.deb
2. List the content of the current working directory to ensure you successfully downloaded the file.
3. Run the dpkg -I command to show information about the deb file.
dpkg -I metasploit-framework_6.2.8+20220720103055~1rapid7-1_amd64.deb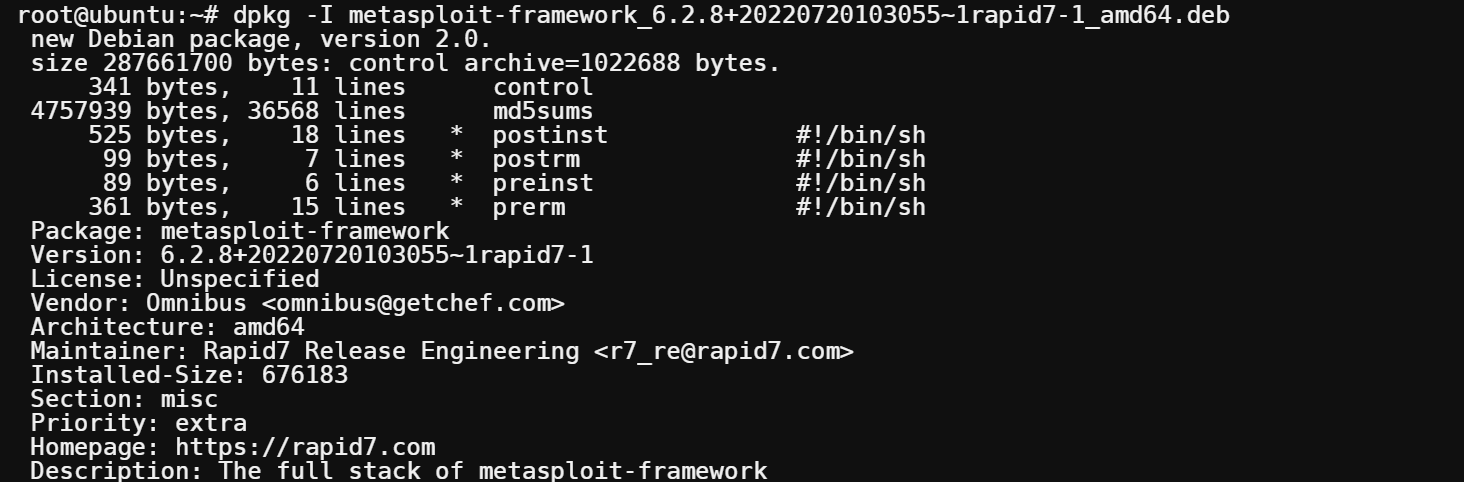
4. Finally, Install Metasploit using the dpkg -i command.
dpkg -i metasploit-framework_6.2.8+20220720103055~1rapid7-1_amd64.deb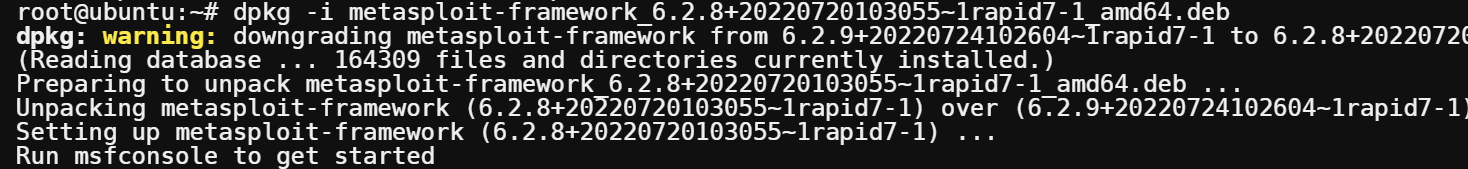
5. Access the Metasploit console and start using it.
msfconsole
Scanning for Vulnerabilities
Now that you have installed Metasploit on your Ubuntu system, it is time to perform a scan. A Metasploit scan has two types: network scans and host scans.
A network scan identifies the available hosts on a network. This type of scan is useful when performing a penetration test on a network to identify the systems available for further attacks.
On the other hand, a host scan identifies the services running on a host. This type of scan is useful when you want to identify the vulnerabilities in a system.
Follow the below steps to run a vulnerability scan with Metasploit.
1. Start the PostgreSQL service. Metasploit saves all of the data it collects in a database. By default, Metasploit uses the PostgreSQL database.
systemctl start postgresql2. Run the below command as a non-root user to initialize a new database for Metasploit.
msfdb init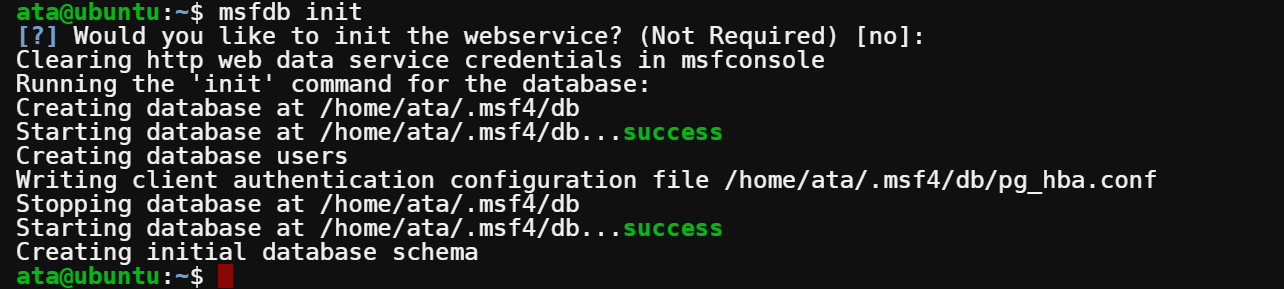
3. Access the Metasploit console.
msfconsole4. Check the database connection. Metasploit uses the db_status command to check the database connection.
db_statusYou will see the following output.

5. Load the msfcrawler module. The msfcrawler module is for crawling websites to find vulnerabilities in web applications.
use auxiliary/scanner/http/crawler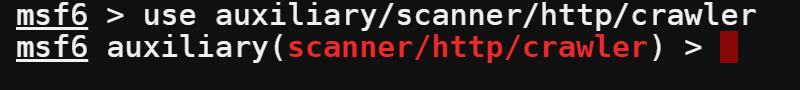
6. Set the RHOST and RPORT parameters. The RHOST parameter represents the target host, and the RPORT parameter represents the port number. In this case, you will scan the localhost on port 9000.
set RHOST localhost
set RPORT 9000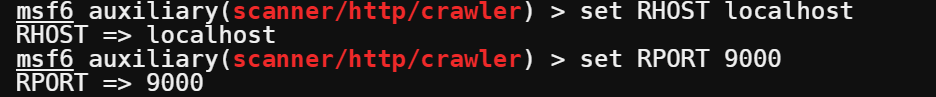
7. Run the below command to start the crawler. The crawler will start scanning the target host and port. This process can take several minutes, depending on the website’s size.
run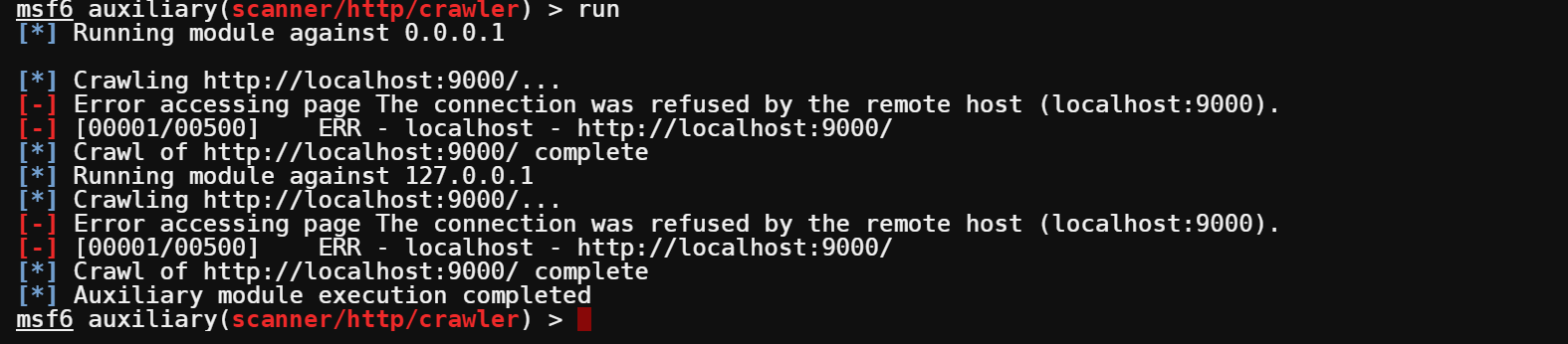
8. Next, load the WMAP module. This module scans web applications for vulnerabilities.
9. Run the wmap_sites -a localhost:9000 command to add the target host and port to the scan list.
wmap_sites -a localhost:9000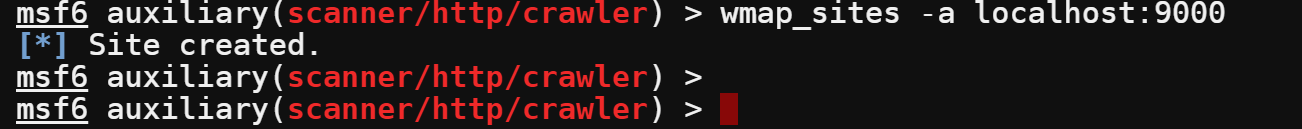
10. List all the available target hosts and ports.
wmap_sites -l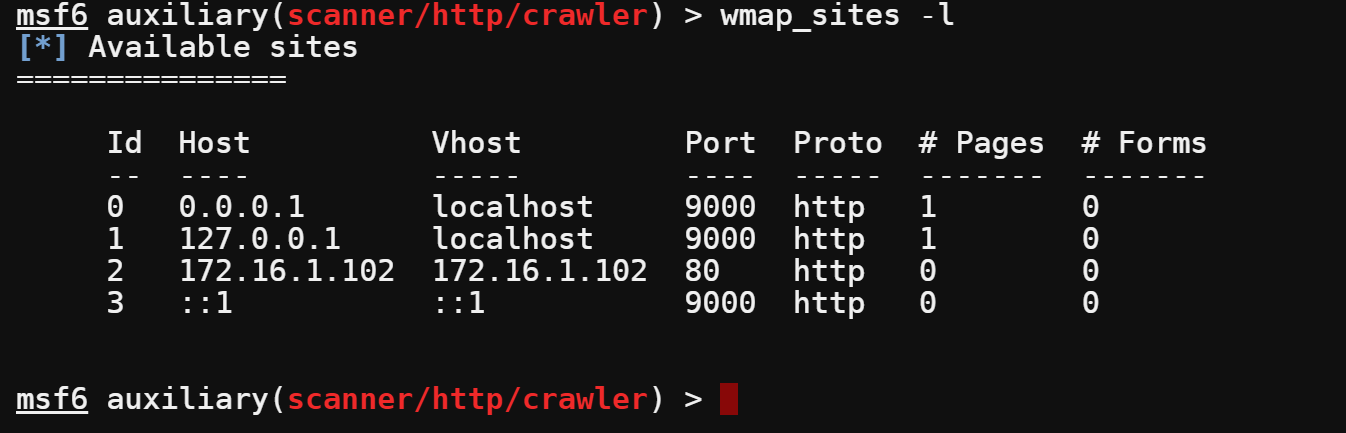
11. Finally, select a target host and start the scan.
wmap_targets -t 127.0.0.1:9000
wmap_run -e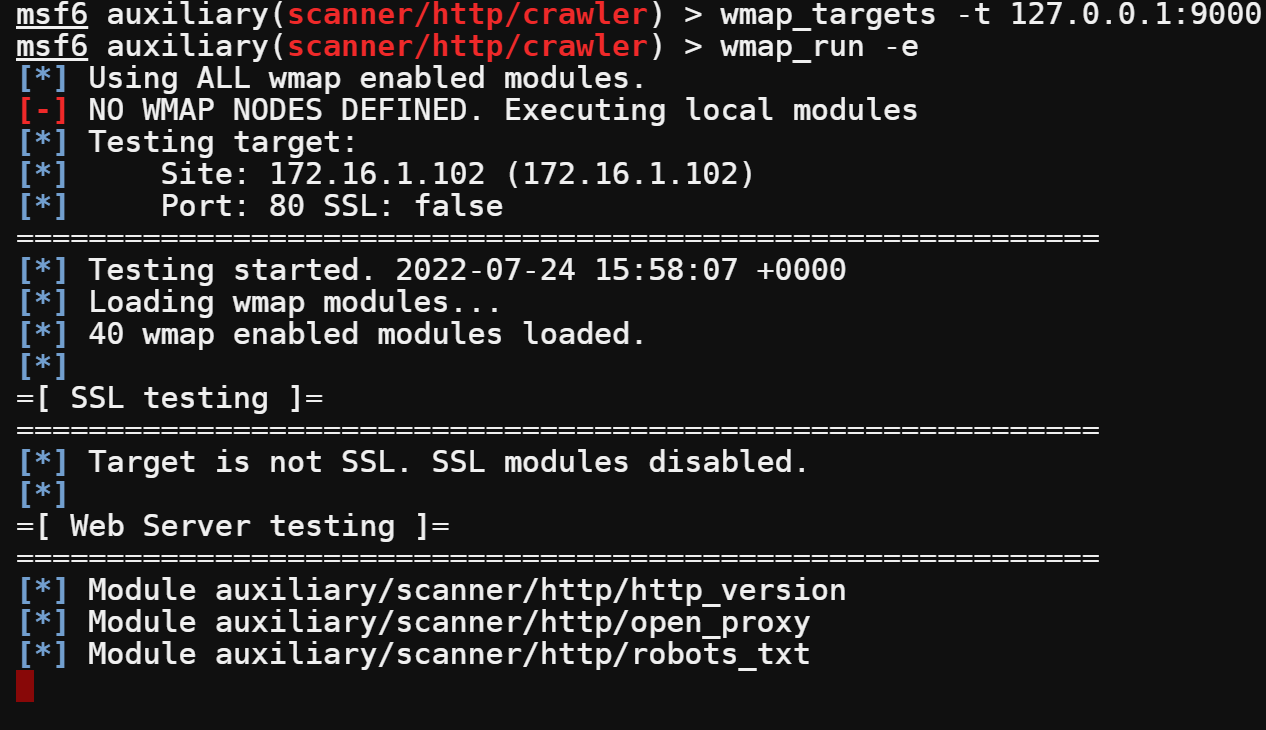
Wait for the scan to finish. This process can last hours, depending on the website’s size. This example takes over two hours to finish.
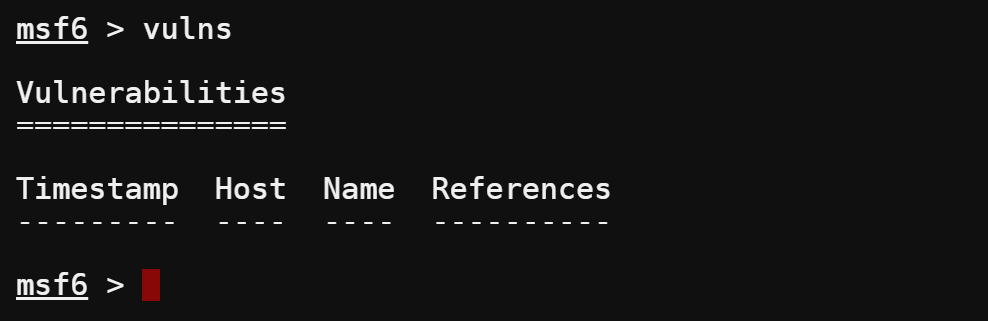
12. When the scan is complete, view the results by running the below command.
vulnsAs you can see, the scan found no vulnerabilities since you are scanning a local host with no web applications. In real-world scenarios, you will get many more results.
TIP: You can use grep, or Linux commands like less, tail, cat. etc., to filter the output.
Conclusion
In this article, you have learned how to install Metasploit on Ubuntu and how to use it to find vulnerabilities in a web application. Metasploit is a powerful tool that can be used for many different purposes. Now that you know the basics, you can start exploring all its features.
With this newfound knowledge, why not start performing penetration tests on your own systems or systems belonging to your clients? Remember to always get permission before starting a penetration test. Otherwise, you could be breaking the law.




